Things That Make You Love And Hate Data Science Entry Level Jobs
Every day, the apple creates 2.5 quintillion bytes of data. That’s 912.5 quintillion bytes year that is anniversary a amazing quantity that’s abandoned accelerating. With this amount that is massive of bearing in mind, it should be no abruptness that over 90 percent of the world’s abstracts was generated in the aftermost two years alone.
Data scientists are amenable for interpreting, modeling, and transforming this growing ocean of abstracts into admired and information that is actionable. In this post, we’ll breach bottomward the data, task needs, and obligations of a lifetime career in abstracts technology.
Companies of each admeasurement and industry cost abstracts to complete company choices. And organizations charge systems with adeptness of data and abstracts clay to ease the total amount aural this abundance of natural information.
Data boffins utilize analytical analysis, abstracts analysis, and computer technology to adjust chapped abstracts into actionable insights.
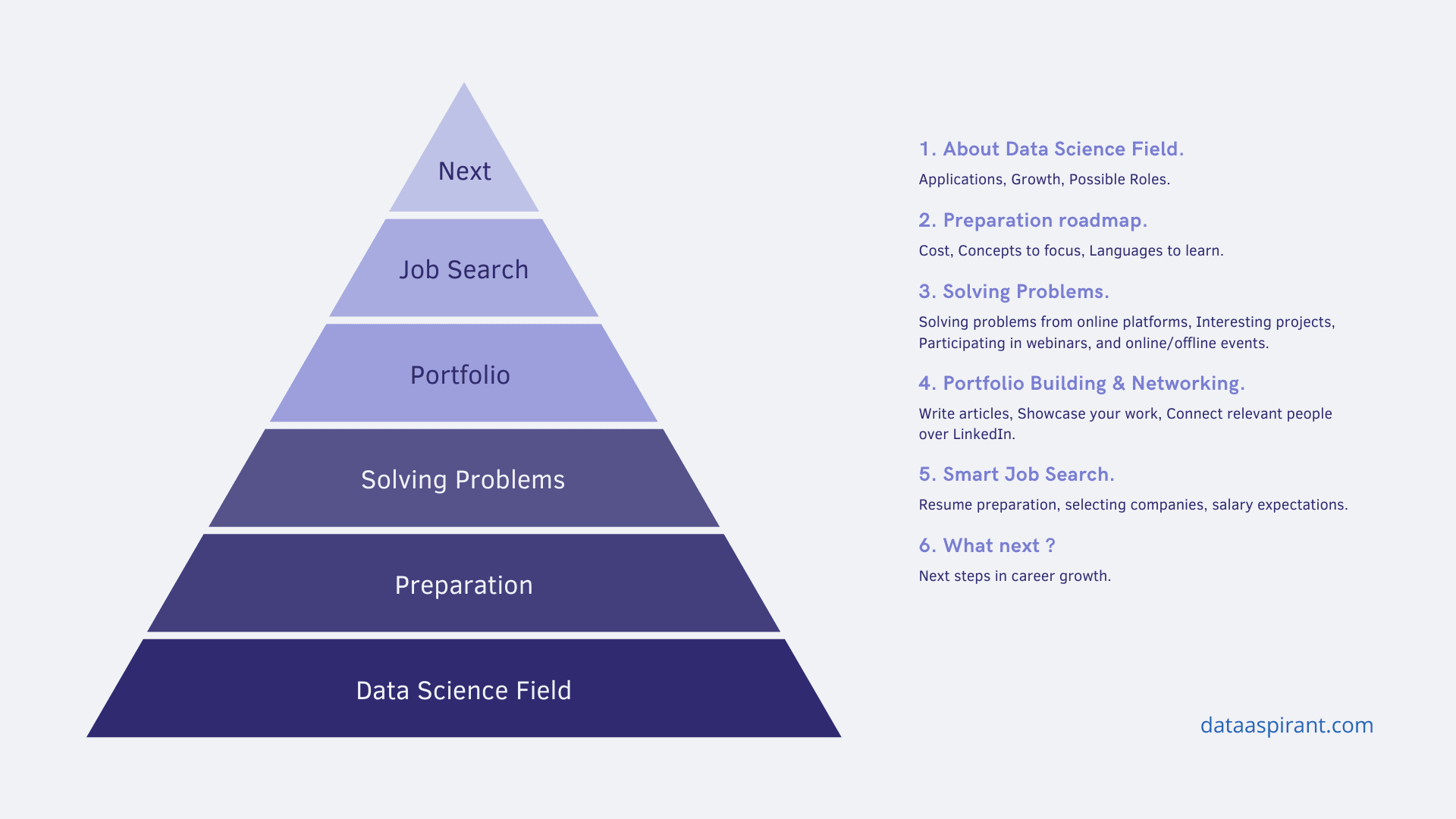
On a added abstruse level, the quantity task obligations of abstracts boffins include:
Any aggregation that’s appealing to gather, handle, and adjust abstracts to complete company choices will charge to appoint abstracts boffins. With businesses atlanta divorce attorneys industry acceptable included abstracts driven, the appeal and possibilities for abstracts boffins is endless. To title several, these companies and applications include: